This will have a huge impact on millions of live websites...
Web browsers, including Google Chrome, Firefox & Internet Explorer, will explicitly flag websites using non-secure HTTP connections. Those three browsers alone, by the way, make up for approximately 93.9% of desktop browser usage at the time of writing.
So does this apply to you? Probably, yes.
To date there’s been no special indicators to signal the real lack of security for non https websites. This simply means that the contents of the webpage/site are passed unencrypted and may be accessible by others, compromising the confidentiality of personal data collected via the Internet.
What is a non-HTTPS warning?
When passing sensitive information over a non-HTTPS domain such as logging into a website or making a payment, users will be shown an obtrusive non-secure popup. These alerts are intended to warn users, who usually tend to overlook the missing “padlock” icon displayed alongside the secure URL on the browser’s address bar, that the information they are passing is not secure.
How will non-HTTPS browser alerts work?
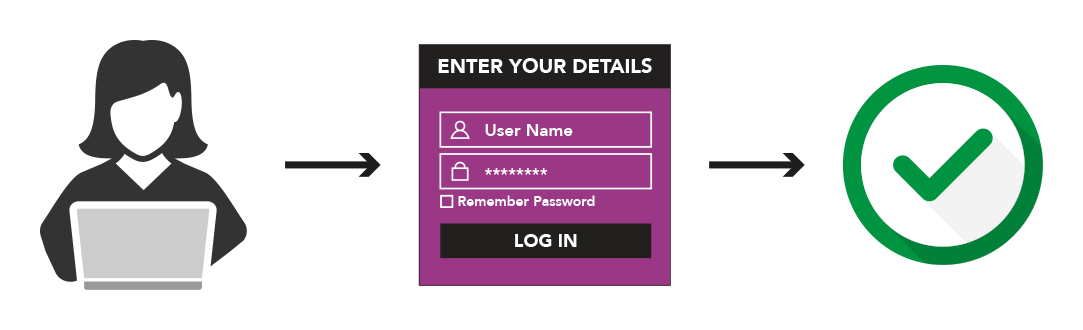
Before browsers introduced non-HTTPS alerts, sending data over the internet was simple. A user would visit a website, enter their personal details into a web form or similar, hit the submit button and the data would be sent, either encrypted via an SSL certificate, or unencrypted.
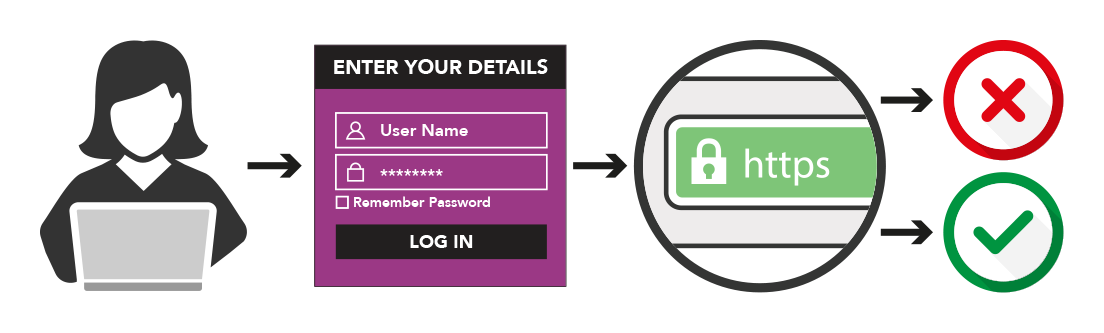
Now, everything will work the same up until the point where the visitor hits the submit button. Next – and this is where everything changes – your browser will check if the domain has a valid SSL certificate. It will then do one of two things:
1. The browser detects that the domain DOES NOT have an SSL certificate. The browser will display a obtrusive popup to the visitor, warning them that the information they are sending via the form is not protected. The popup will ask the visitor if they would like to proceed anyway – it’s then down to them if they trust your website.
…or…
2. The browser detects that the domain DOES have an SSL certificate. The information entered by the visitor will be passed over an encrypted (SSL) connection and everything will be fine.
What impact will this have on conversions?
The impact of these non-HTTPS alerts on online businesses will be huge, considering the fact that a majority of them are yet to move to HTTPS. Conversions will get more challenging as users won’t be willing to part with sensitive information, fill out any online forms, or complete checkouts when they see a browser security alert flashed on the screen.
Websites that restrict access or transactions based on login credentials will need to do so over a secure connection, stay away from browser security alerts, and also guarantee the authenticity and integrity of the site by switching over to HTTPS.
As a step towards making the web more secure for users, web browsers intend to issue a warning when sensitive data is passed over a non-secure (non-HTTPS) domain.
Will SSL warnings extend to private browsing?
Subsequently, browsers such as Google Chrome will proceed to label HTTP pages as “not secure“ in “incognito mode” (private browsing), and further extend the feature to regular browsing mode as well.
When will we first see non-HTTPS alerts?
Pretty much straight away.
Google Chrome will introduce alerts on websites which are not protected by an SSL certificate in January 2017. It’s expected Firefox and Internet Explorer will follow very quickly.
These ‘not secure’ alerts will surely have a negative impact on user trust and damage conversions, at least initially before the website administrators realise their online turnover has dropped off the edge of a cliff due to users being put off by the non-secure popup.
Say goodbye to SHA-1
Also, website connections protected by SHA-1 SSL certificates may soon be redundant, as this algorithm is no longer secure against advanced computer and mathematical processing capabilities of today. According to Google, the very first signs of weakness in the algorithm were evident over a decade ago, making it imperative to adopt newer cryptographic technologies to strengthen data encryption.
Google will withdraw support for SHA-1 certificates in Chrome 56 set to release by the end of January 2017. Chrome will no longer trust certificates based on the SHA-1 algorithm, and users visiting a site using SHA-1 certificate will be greeted with an interstitial warning. Such a move could prove a cause of concern for millions of websites that are not ready for the mass boycott of SHA-1 by the different browser makers. Microsoft will withdraw support for SHA-1 certificates from February 2017, blocking access on both Internet Explorer and Edge. From early next year, Firefox will also flag a non-secure connection when users access a website protected by SHA-1 certificate.
Do you already have an SSL certificate that’s been in place for some time? You should check if it’s SHA-1, and if it is, do something about it. It’s really easy. Just visit shaaaaaaaaaaaaa, input your domain and it will tell you.
Websites will need to plan ahead to migrate from SHA-1 to SHA-2 to strengthen security against malicious breaches, escape the blockade, retain the trust of consumers and remain in business. As for small businesses and personal websites that may not really contain any confidential data, obtaining a free TLS certificate will prove beneficial in many ways. This certificate not only ensures encrypted traffic on the web, but also validates the authenticity, identity of target sites, and reportedly works in favour of the website when it comes to SEO rankings.
Conclusion
The non-HTTPS security warning is here and there’s no way to stop it. If you don’t collect a user’s sensitive information over the internet you probably don’t need to worry about it. But if you do, you should contact your website administrator to install an SSL certificate as soon as possible.
If you need an SSL certificate or are unsure if you have one, please contact us.




